The average cost of a single security breach in Germany is $4.85 million in 2022 (IBM 2022). System-critical industries such as healthcare and finance are suffering particularly badly from the costs of data theft. We spoke to the experienced Head of CyberSecurity at Hays, Michael Beaupre about the current state of the fight against cybercrime.
Between military and business world- What is the battle in cyber security?
Prior to your position as CISO at Merck, you served as a cyber expert for the U.S. military.
Why are we talking about a “fight” against cyber crime, can you give the readership here some insight into the status of the fight?
Michael Beaupre: A “fight” Is such a fitting description of cyber security and our combined efforts against cyber crime. Cyber security is not a static discipline, it is an ongoing battle between opposing forces. Those who are committed to protecting and those who are committed to exploiting.
With every new innovation and every new technology, comes a new risk or vulnerability. Those who exploit, actively search for these opportunities and take advantage of weaknesses. Those who exploit, actively search for these opportunities and take advantage of weaknesses. Those who protect, respond with countermeasures to close the vulnerabilities, prevent exploitation, and deploy Innovative methods to mitigate the risk. In response, the exploiters come up with methods to bypass or work around these defense measures. It Is an ongoing and perpetual fight that never ends and always escalates.
Who are the actors? Are they criminal individuals or can we talk about organized crime?
Michael Beaupre:Exploiters, or Adversaries, come In various shapes and sizes and take on many different forms. For example, State Owned Enterprises (SEOs), Hacktivists, Organized Crime Syndicates, Individual Threat Actors, Script Kiddies, Anarchists, and more. The MITRE attack framework (MITRE ATT&CK®) is one of my favorite resources to help us understand the complexities of the fight.
Can you explain what such frameworks offer and how you use them?
Michael Beaupre: It is based on the real-world tactics and techniques most commonly used by adversaries and describes the best countermeasures to apply in any given phase of the fight. It provides truly deep, meaningful, and practical insights into the ongoing fight across a multitude of dimensions. Most importantly, the overarching purpose is simply bringing communities together to develop more effective cybersecurity. Building, educating, and equipping coalitions of allies to help us protectors win the fight.
How are companies positioned with regard to cybersecurity?
Michael Beaupre: That really depends on the perspective you approach it from and what country you view that question from. Cybercrime Magazine, estimates cyber crime will cost the world $10.5 Trillion Annually by 2025. It further explains and estimated 3.5million unfilled cyber security positions world-wide.
We can find several other reports with mind blowing facts and figures that can be scary when taken out of context. Cyber crime magazine and similar organizations do an excellent job providing important facts and figures to help us understand the fight; it is a critical and valuable service. But we need to see the full context of what they bring us and understand it from a broader perspective. All too often people will only use pieces and parts to advance their narrative.
From a narrow perspective, it looks like we are losing the fight, and the adversaries are destroying the protectors. But that isn’t the full story. Just like with any conflict the full picture needs to be explored and understood. It Is a fierce and complicated fight, and we are struggling in many areas. But we can’t lose sight of the progress we have made. If we do, we could lose hope and give up. Then we will surely lose.
For example, Derek Brink provides insightful advice on understanding true risk through statistical analysis of the latest cyber headlines and figures. Using the median instead of the average and understanding the distribution of the data can provide valuable perspectives when speaking about cyber to the board and other business leaders. It paints a very different picture than the headlines.
We must also remember that we made significant advancements over the decades. Kevin Mandia is a pioneer in the industry and a true fighter who never gives up. The revolutionary advances in threat Intelligence he established through Mandiant have helped us win significant battles in this ongoing fight.
Where do companies need to set priorities?
Interview with Ron Bushar, CTO at Mandiant
By loading the video, you agree to YouTube's privacy policy.
Learn more
Hays is meeting with cyber security leaders from around the world to hear their insights on today’s challenges. We learn about the cyber risk profiles of the companies they work with, how global events have impacted the way they operate, and hear how they find and develop talent for their security teams.
In this episode, Michael Beaupre talks with Ron Bushar, Senior Vice President and Global Government CTO at Mandiant. Ron shares his experiences on the front lines of cybersecurity and discusses how organizations need to set their priorities.
Michael Beaupre: And like any fighters, Kevin and his team of professionals have taken their share of punches while fighting on the front lines. But they keep on fighting. The recent acquisition of Mandiant by Google Cloud will further equip and enhance their capabilities to fight on a broader scale.
What are corporations doing to fight cyber crime?
Microsoft, Apple, Amazon, and other tech giants are investing heavily In the fight to build our competitive edge against cyber adversaries on a global scale:
Amazon will make its cybersecurity awareness training available to the public for free.
Microsoft will invest $20 billion over five years, a four-fold increase from current rates. They will make available $150 million in technical services to help federal, state and local governments update security systems.
IBM will train more than 150,000 people in cybersecurity skills over three years and will partner with historically black colleges and universities to create a more diverse cyber workforce.
Google devoting $10 billion to cybersecurity over the next five years and will help 100,000 Americans earn industry-recognized digital skills certificates that could lead to high-paying jobs.
I often speak about hurricanes as cyberstorms, cyber warfare, and other metaphors that require joint communities and coalitions to overcome catastrophe, conflict and strife. I do this because we all understand that innovative technology is a key component of winning this fight. But we need to embrace the paradigm that our true success comes from the joint communities and global partnerships we establish. That is how we win when fighting against an advanced and persistent enemy.
As they said In the wild-wild west, when you circle the wagons to protect each other, the guns point out and not In. We can only win if we come together to fight as allies and not as competitors. We see more and more tech giants, Industry leaders, and Influential government leaders joining forces to share cyber security capabilities and capacity. That Is the key to winning, and that’s why I joined Hays.
We are not alone in this fight. We are in it together and we are in it to win it.
Artificial intelligence and automation in cybersecurity: realistic or futuristic?
Artificial intelligence and automation are seen as a great opportunity to save costs in the cyber security space. Economic losses due to security breaches in companies that have fully implemented security AI and automation are significantly lower.
Is such an implementation even realistic in terms of resources for most companies?
Michael Beaupre: Again, that Is completely based on your perspective. I would ask the question differently. Can companies afford not to Invest in these capabilities?
Cyber crime cost the economy an estimated 10.5 trillion annually. Now, compare that with the total global investment in cyber capability of 173 billion euro. We are significantly underinvesting in our defense capabilities. But that trend is changing.
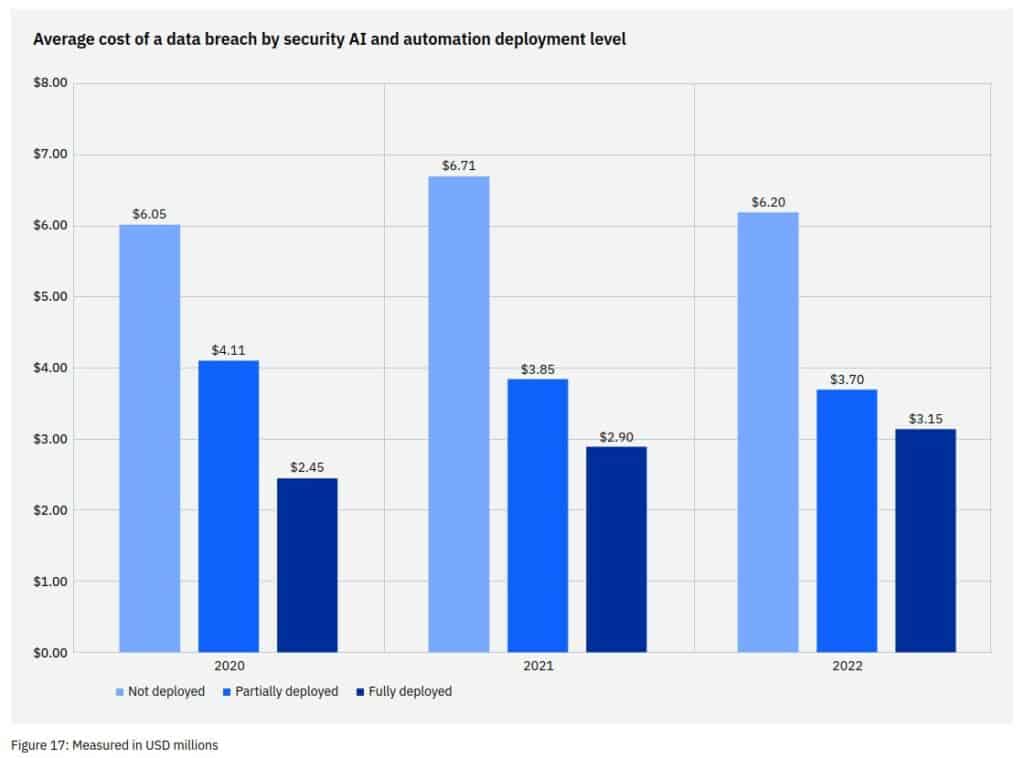
IBM publishes an annual cost of a data breach report. This year Is the 11th report and it provides significant Insights. One highlight demonstrates the value of AI and automated solutions as follows:
Data breaches in organizations without security AI and automation cost an average of €6.2 million compared to an average of €3.15 million in organizations with fully implemented security AI and automation.
This corresponds to a cost saving of 65.2 percent (3.05 million euros)!
As you rightly said this statistic is highly valuable. It is worth studying them using the methods recommended by Derek Brink to assess the real benefits. In any war, the value of advanced technologies is clear. Let’s imagine two opposing nations in a war: One side invests in tanks, long-range missiles and stealth bombers. The other in clubs, pitchforks and torches for their compatriots. Which side is most likely to win this war? Our common adversary is investing in cutting-edge technologies for its attacks and will continue to do so. If we don’t keep up, the opponent will gain the upper hand. This is an arms race in strategic and long-term cyber warfare. As such, we must view this conflict.
What does this mean for freelancers? Are you familiar with modern cyber technologies? Do you keep up with the latest innovations and acquire the appropriate skills in using these tools? Are you building and marketing your leadership and mentoring skills? If this is the case, your value in this war also increases significantly. This in turn affects your day rates as well as your chances of winning projects.
Tackling the skills shortage in cybersecurity.
Currently, 62 percent of companies are understaffed to meet their IT security management needs (IBM, 2022). Many companies are struggling to fill positions on their IT security teams. The shortage of personnel and the extremely high demand are expressed, on the one hand, in hourly rates and, on the other hand, in the significantly higher workload of the existing specialists.
As Head of Cyber Security at Hays, you have made it your mission to close the skills gap in this area.
What do you see as the biggest levers in this project? What successful strategies are companies pursuing on the market?
Michael Beaupre: I see closing the cyber skills gap as a complex challenge. It is NOT just about hiring more people. The right people with the necessary skills must be found to correctly deploy constantly advancing technologies and lead the teams responsible for them. We need forward-thinking leaders who understand the current war.
Hays analyzed 17,000 open cyber jobs across Germany with the following results:
Cyber Experts (#1), Cyber Consultants (#2), and Security Engineers (#3) are the three positions with the highest vacancies.
Leadership positions are the fourth most sought after, including CISOs and product managers, as well as cybersecurity governance and compliance managers.
Security officers for IT and data protection land in 5th place.
Engineers and network security experts take 6th place.
There is often talk about the shortage of skilled workers in technical fields. Articles talk about how difficult it is to get to the level of technical geniuses. However, we are overlooking an important aspect of the skills gap: Leadership and management.
In my opinion, it is easier and more efficient to teach highly skilled leaders how to lead cyber experts than to try to teach leadership skills to highly technical cyber experts. Instead of relying on limited capacities of technical experts to fill leadership and management positions, we can meet these needs with forces from other closely related fields. As a community, we should look more closely at this aspect of the skills gap.
Throughout my career, I have been able to use simple approaches to solve complex challenges. Two key factors must be considered when closing the skills gap.
We just talked about the first one: Selecting the right skills and the right leaders. The second factor concerns the use of modern technologies, artificial intelligence and automated solutions as a multiplier. We should not only meet the need for technical resources and management and leadership personnel, but also help reduce the overall manpower requirements for this war through automation and technology.
Among other things, investing in modern technologies helps secure an advantage over the enemy’s “cyber tanks” and “long-range cyber missiles.” This means investing in skills needed to manage and deploy these technologies. And that with strong leaders who are appropriately empowered and qualified, we align these competencies with those responsible within the company. These objectives are complementary, not competing.
The task is demanding and extensive. If it were easy, there would be no shortage of cybersecurity professionals.
Global strategic partnerships with tech giants, innovators, universities and institutions are needed to acquire both talent and technical skills. This trend is becoming increasingly clear, and I see it as one of my tasks at Hays to further accelerate this development.
We need to act as partners to drive this positive trend by training and educating each other and demystifying the cyber industry. It’s not an elitist industry that’s hard to get into and is exclusively tech geeks and hackers. We need to make it clear to executives that the cyber industry is more about business risk, leadership and awareness than technology. As mentioned earlier, we need technology and innovation – but these are only part of the solution. Strategic investments in cybersecurity are relevant from a business perspective and are supported by executives who recognize how significant the fight in this area is.
One of my favorite quotes from Sunzi’s“The Art of War” describes a fundamental truth of the cyber environment:
“If you know yourself and the enemy, you need not fear the outcome of a hundred battles. If you know yourself but not the enemy, you will suffer defeat for every victory you win. If you know neither the enemy nor yourself, you will be defeated in every battle.”
How does this translate to cyberwar?
First of all, we must understand that we are in a war.
Second, we must commit to winning this war.
And third, we must gain the understanding, skills, and allies necessary to win.
We need to understand not only ourselves and what makes us successful as a company, but also the enemy and what they are trying to achieve in this war. In this way, we need not “fear the outcome of a hundred battles”.
The advantages of this approach are clear to see. According to IBM, the average cost savings of a data breach is 550,000 euros in companies with sufficient skilled personnel compared to other companies. At the same time, I cannot emphasize enough that “sufficient staff” is not limited to headcount. It all comes down to the appropriate capabilities, matched precisely to the company’s risk profile and the biggest threats in the industry being protected. Or, in other words, a company staffed according to Sunzi’s principle mentioned above.
Career change in the field of cyber security as IT freelancer
Could the huge demand for cybersecurity specialists also provide an opportunity for career changers?
What advice would you give to IT professionals looking to start freelancing in cybersecurity? What previous knowledge is necessary?
Michael Beaupre: I think I’ve already talked about that at length. In short, don’t be afraid and don’t be intimidated if you want to make the lateral move. It’s not as complicated or one-sided as some people in the industry make it out to be. There are many ways and methods to develop and educate yourself. One of IT Freelancer Magazine‘s recent articles on this topic provides a good starting point.
But most importantly, you should Get in touch with a Hays cyber expert. and benefit from our experience and expertise in planning your entry together. We are currently in the process of establishing several partnerships with representatives from mathematics, computer science, natural sciences and technology (MINT) in various countries. In addition, we partner with leading cyber experts in the industry who can sponsor the transition from your current area of expertise. Contact us and we will help you make contacts at the right level to fulfill your goals and desires.
Entry in the field of cyber security?
Hungry for red-hot cyber insights?
Take 5-10 minutes to participate in our cyber security survey!
How will companies respond to cyber threats in 2022? What challenges do your cybersecurity colleagues face in finding and retaining the right talent? How much is spent on cyber teams worldwide?
Hays focuses on your cybersecurity issues and challenges and publishes a Cyber Security Report based on your input.
Fill out our short survey and we will send you the results in the spring of 2023.
About Michael Beaupre

Michael Beaupre is a leading technology expert with over 25 years of experience advising international public sector institutions, DAX-30 companies and mid-sized international firms on strategic technology initiatives. He is a specialist in digitalization and IT transformation and a thought leader in cybersecurity, organizational risk management and IT compliance.
Its teams deliver cost savings and profitability through practical technological innovations in a variety of areas. As a freelancer, he consults globally to small and large companies with 20 to 220,000 employees in the medical, pharmaceutical, biotechnology, translation and manufacturing industries.
